All-in-One Suite
for all Your Corporate and Legal Activities
Five Integrated Modules, Designed for All Your Needs
Digital solutions for your governing bodies
From agenda preparation and document sharing, all the way to meeting management, voting and automatic minutes generation, the Board Portal is a comprehensive solution that enables both board members and general secretaries to collaborate in a dedicated and secure environment.
A 360° view of your entire contract lifecycle
Take control of your contract management and oversee each phase of your contracts with one centralized digital solution. Leverage the power of advanced Artificial Intelligence, with user-friendly features, for a secure and streamlined journey through your contract’s lifecycle.
Realtime data to manage the company’s legal operations
Get a complete view of all entities and centralize all your legal data in a dedicated digital solution. Simplify the access to real-time and historical information about your group to stay in control of your organization, improve cross-departmental collaboration and focus on what is valuable.
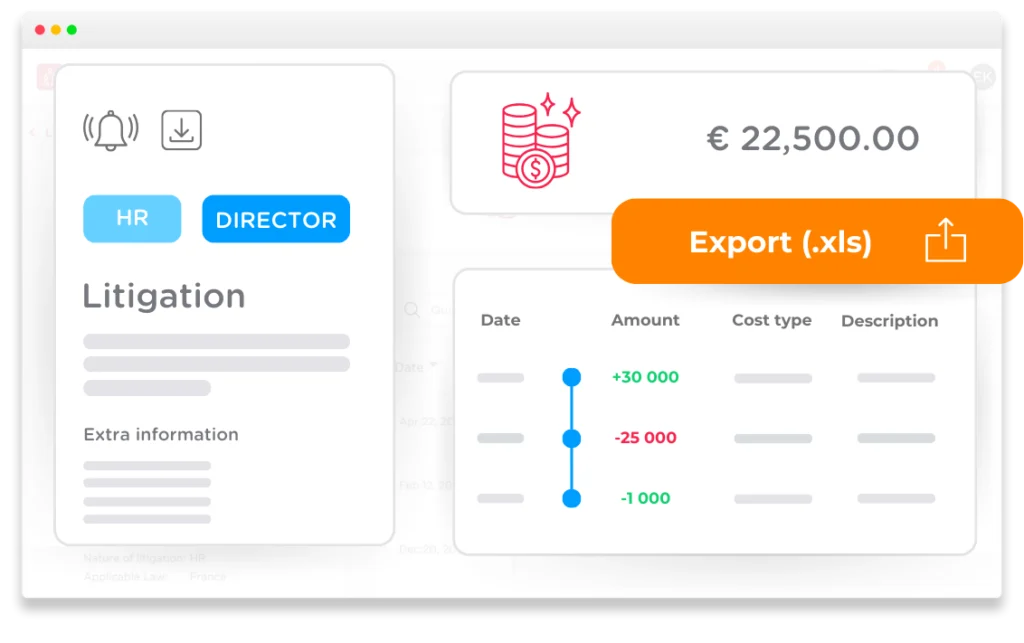
Limit risks with controlled monitoring of litigations
Optimize your organization’s litigation and dispute management to limit risks and lower costs. Manage and analyze the financial impact of past procedures and anticipate current and future ones with a centralized solution that will improve your procedure performance.
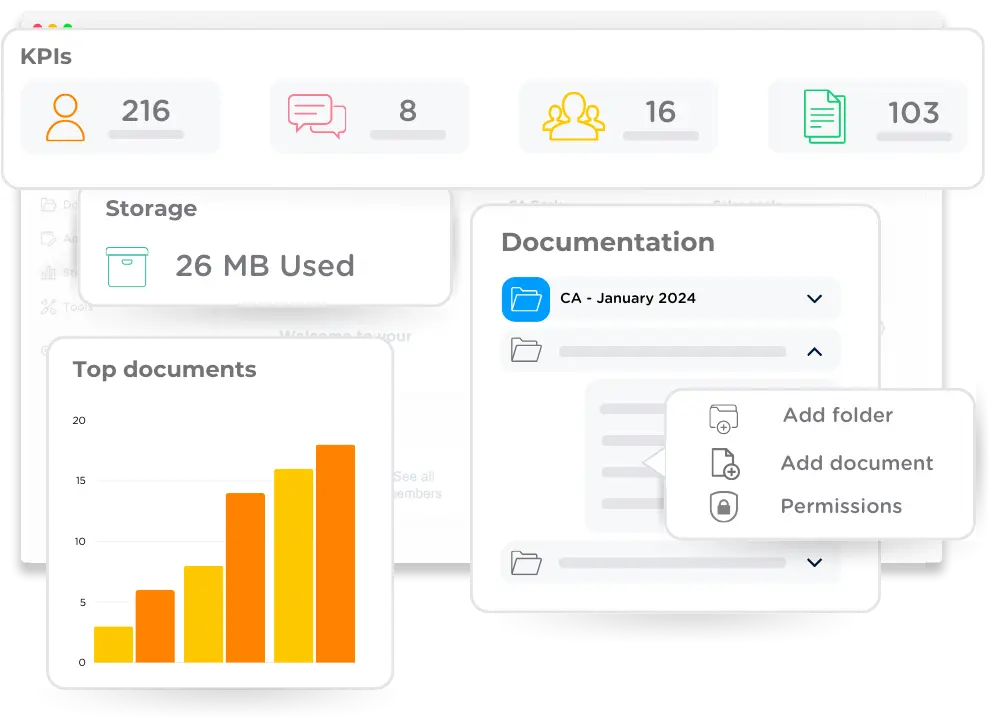
Highly secure and centralized sharing of confidential documents
Optimize access to information with an unlimited storage repository. The Documentation Library is a secure solution designed for all types of users and projects to digitally archive, organize, and share sensitive and confidential documents, either internally or externally, with full traceability.
A Single Platform With All the Features You’re Looking For
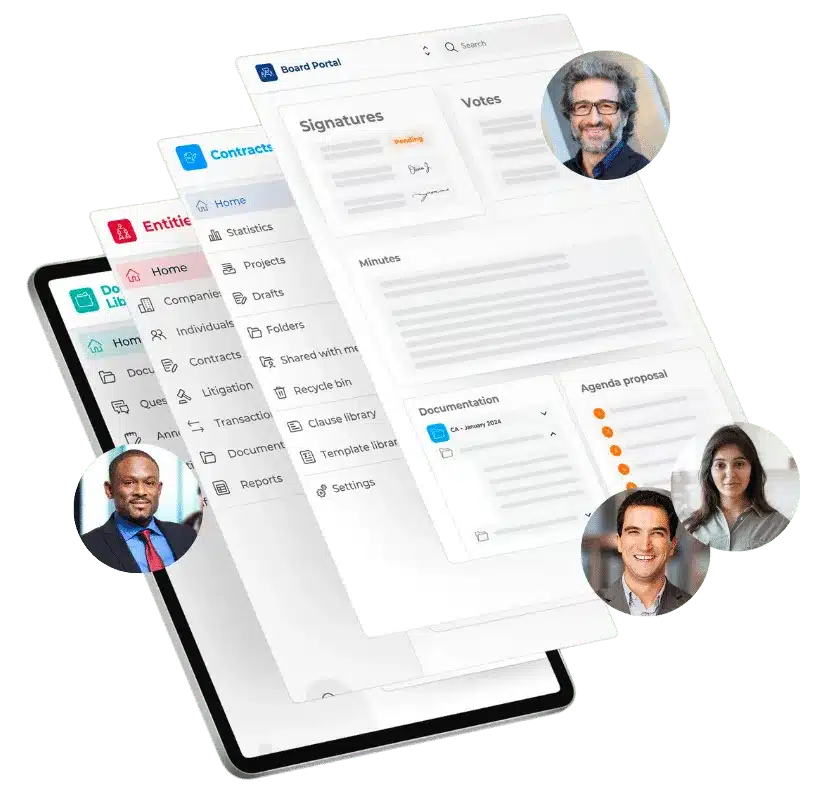
Our Suite is Designed for you
We are dedicated to supporting your digital transformation journey. DiliTrust Governance empowers each user to streamline their operations, boost performance, and minimize risks across the board. Whether you’re a small team aiming for quick structuring and development, a larger organization seeking to enhance collaboration and data management, or a large enterprise focused on secure contract management, we’ve got you covered. With years of experience helping organizations like yours, we understand the diverse needs of different teams. Let us guide you towards greater efficiency, collaboration, and success.
Equip your legal team with our tailored suite designed for General Counsels, Legal Operations, Legal Affairs, and legal professionals. Improve contract management, regulatory compliance, and litigation support while streamlining internal processes and risk management practices.
Elevate your governance strategies with our intuitive platform for board members, directors, C-suite executives, and key decision-makers. Manage board duties, access information securely, and promote collaboration for informed decision-making before, during, and after meetings.
Maximize operational efficiency in finance, HR, procurement, and more, with our comprehensive solution. Empower teams to optimize workflows, enhance communication, and drive productivity, while ensuring compliance and minimizing risks.
Simple
At the heart of our suite lies simplicity, meticulously crafted to ensure that every user, from legal professionals to executives, can navigate the platform effortlessly. The intuitive interface and dedication to a paperless system make navigating the platform a breeze, allowing for seamless access and operation. By simplifying corporate governance tasks, our solution promotes efficiency and productivity for all stakeholders involved.
Flexible
Featuring five integrated modules, the DiliTrust Governance suite is designed to adapt to organizations of any size. Whether you’re a small team looking to streamline operations or a large enterprise seeking comprehensive solutions, our SaaS platform can be tailored to meet your specific needs. With seamless integrations and customizable features, we empower organizations to work smarter, not harder.
Reliable
At DiliTrust, we prioritize the security and reliability of our platform. With robust data protection measures and security protocols, our suite ensures the confidentiality of your sensitive information. Centralizing all your governance activities in one secure location, our platform offers peace of mind, knowing that your data is safe and accessible to all stakeholders whenever they need it.
Complex, Sturdy and Sensitive Corporate and Legal Information Made Simple, Flexible and Reliable
At DiliTrust, we’re all about making your experience smooth and hassle-free. Our platform ensures that every interaction is intuitive and effortless, so you can focus on what matters most. With tailored solutions, we empower legal and corporate teams to shine, becoming indispensable assets in their organizations.
We’re here to boost your confidence and expertise, simplifying even the most complex legal tasks. And rest assured, we’ve got your back when it comes to security, ensuring your legal operations are safe and sound every step of the way.
clients already trust us
countries where DiliTrust operates
of customers recommend us
Explore a Complete Solution Tailored to Streamline Your Activities
Request a demo today and experience a seamless transformation in your legal and corporate governance operations with DiliTrust’s Governance suite.