When it comes to contracts, in this age of all-out digitalization, we have every right to wonder about the protection of this particularly sensitive data (especially when we frequently hear about malware* in the press). That’s why at DiliTrust, we wanted to talk to you about security.
In this article, we share our tips to help you protect your online contractual data from threats.
The Cloud: your data in the cloud
What is the Cloud?
Today, many technologies are accessible via what is known as the “Cloud”, or more precisely “Cloud Computing”. We also speak of IaaS (Infrastructure as a Service) and SaaS (Software as a Service).
In practical terms, the Cloud is a way of providing computing, storage and network resources in the form of an online service. Very widespread today, companies often resort to it, for example for their ERP, CRM or LegalTech.
What’s behind the cloud craze?
This success is no accident. In fact, the Cloud offers many advantages.
To name but a few:
- Cloud computing doesn’t require any complex installation or infrastructure, and usually all you need to access your software online is a browser and an account. In other words, you don’t need to be a computer scientist!
- The Cloud is accessible anywhere, anytime, on any device (mobile, tablet, PC). Deployment is easy for geographically dispersed teams: no need to open servers or manage remote installations. From France to Brazil, deployment is just a click away!
- The Cloud facilitates document sharing and collaborative working: no more endless, confusing email exchanges or screen sharing… You and your colleagues use the same working environment, the same tools, in real time and in a simple way.
- Cloud software solutions are often intuitive, relatively easy to learn, scalable and upgradeable: no need to update, manage obsolete versions or pay for upgrades. That’s the “all-inclusive” advantage: you’re always on the most recent version, and always up to date with your security updates.
The Cloud: is there a risk?
Despite its many benefits, a logical question is likely to burn the lips of its users: “if I’m connected, is my data at risk?” First of all, no more than on your computer, which is itself connected to the rest of the web via various tools such as your mailboxes, your browser, etc. Don’ t forget that security also depends on you (updates, controls) and the vigilance of your IT teams (update cycles, internal technical audit, etc.).
Secondly, the growing success of the Cloud over the last few years provides a first clue: it now enjoys demanding standards and security measures.
But which ones? That’s a good question.
And therein lies the solution for the user: before subscribing to online software, the best way to ensure that your data is protected is to ask the right questions. Let’s see what they are.
Questions to ask your software partner to ensure the security of your contractual data
The infrastructure
Infrastructure is, in a way, the skeleton of your information systems: servers, network, software, data… it’s the ecosystem that ensures the smooth running of your digital tools and, consequently, your day-to-day work, if you’re used to using a computer! Security starts here.
So ask your partner about the measures in place at infrastructure level. For example, is there an Intrusion Prevention System (IPS )? This system analyzes network traffic, detects cyber-attacks and helps block them.
Another example: are there any anti-flooding measures? Anti-flooding measures are designed to prevent the sending of large quantities of obsolete data to flood a network and render it unusable.
Or: is the architecture multi-tier? This is an IT architecture in which an application is executed by several distinct components. In other words, an infrastructure based on several independent tiers. This is known as segregation: imagine compartments separated by fire doors to prevent the spread of a fire… This means that the most sensitive services (e.g. your database) are not directly exposed to the web, thus reducing the risk of data leakage in the event of a security breach.
In the three-level example below, there are :
- the user interface in front of his workstation (front),
- server applications containing business rules and accessing data stored in the database (back),
- the database itself.
The three levels are separated by “firewalls” or “firewalls” designed to protect network information, filtering inputs and controlling outputs according to administrator-defined rules.
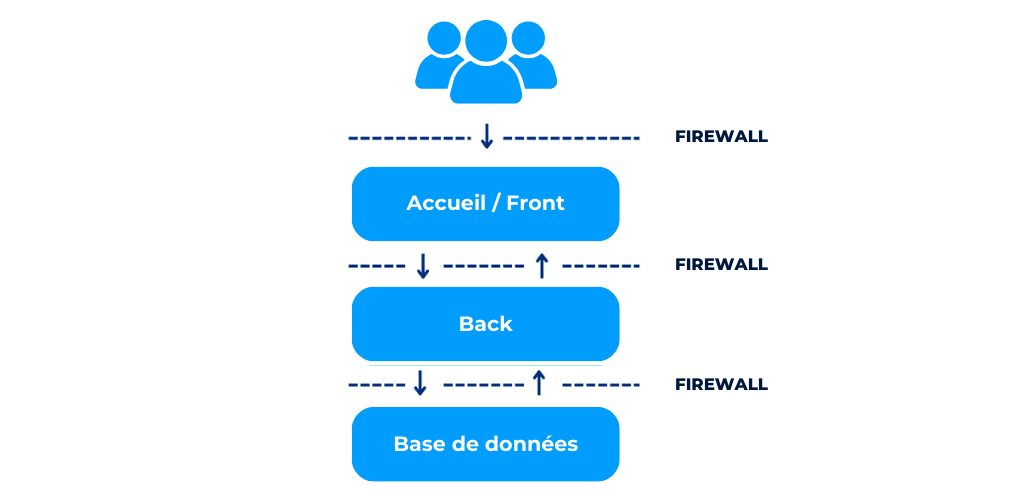
This is important, because in the event of a ransomware attack on your company, this malware will not be able to spread to your database. Your contracts will therefore be protected from this type of attack.
DID YOU KNOW?
An additional security measure, double authentication consists of associating a password known to the user with a connected object in his possession, such as his telephone. With this measure, in the event of a password leak, the user’s account remains protected from intrusions!
The data
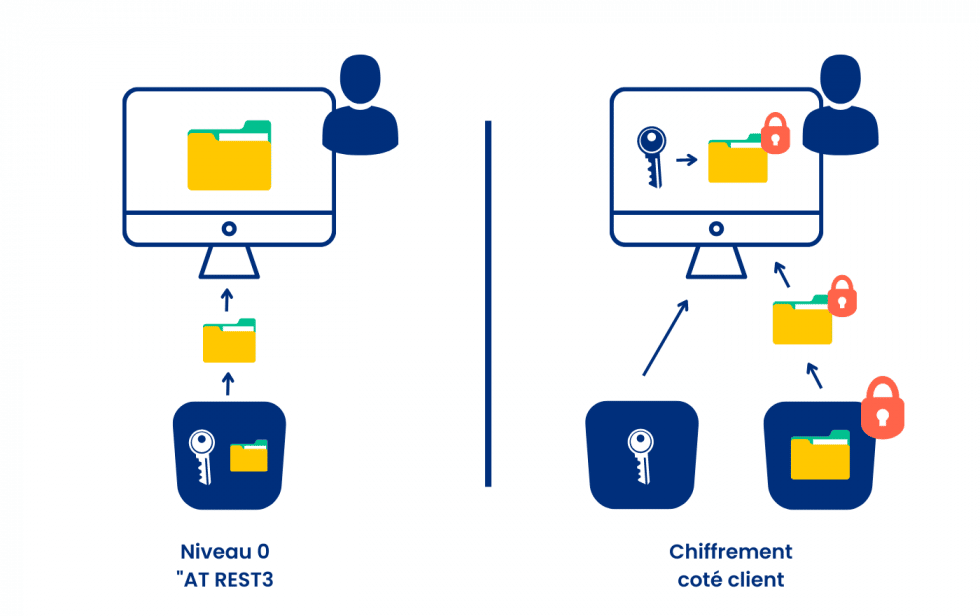
After infrastructure, it’s time to think about protecting not only your data itself, but also the “pipe” (channel or protocol) that carries it. This is where encryption comes in. Encryption is the process of converting data from a readable format to an encoded (or encrypted) format, which can only be decoded after decryption using a key. Three questions then arise: what is really encrypted? when is the document encrypted? and where is the key stored to decrypt it?
Protocol protection
To help you understand, we’ll give you our own example. At DiliTrust, all data transmissions are encrypted using the TLS 1.2 (Transport Layer Security) protocol, which complies with the highest security standards and ensures server-side and client-side authentication, confidentiality and data integrity. This prevents a malicious person eavesdropping on the Internet connections between your company and our servers from being able to see the data in circulation.
Data encryption
By encrypting the data itself, you enhance their security. At DiliTrust, the document deposited in the application is encrypted with a unique key from the customer’s browser, and remains encrypted from end to end until it is next viewed by the customer. At no point is data transmission or storage unencrypted. In addition, each customer can create document-specific encryption keys via a key management service hosted on a different infrastructure, or can set up their own key management service.
The organization
Another point to watch out for is your software partner’s organization. And yes, beyond a technology, your partner is also a company with its own staff, its own service providers and its own tools. A good way to ensure that your data is in safe hands is to find out how they are organized. In other words, what resources are in place to guarantee the security you’re looking for?
For example, you can find out about certifications and audits carried out, as well as operational practices within the company.
Technologies and malware are constantly evolving. The best way to ensure the security of your data is to regularly review the technical and organizational security of your information system. The same applies to software publishers: regular penetration tests and feedback are essential. It’s also a way of questioning your own organization: when was the last time you carried out an intrusion test?
Would you like to find out more about security at DiliTrust? See our dedicated security page.
Backups
You’ll sometimes hear the term “back-up” used. This means making regular back-ups (or security copies) of your data. Here, we’re no longer talking about prevention. In fact, two precautions are better than one: in addition to the protection measures in place, your LegalTech must also think about recovery measures. It’s an extra measure of confidence that you can expect from your partner.
Backups reinforce the security of your data by meeting a simple challenge: to be able to recover it in the state it was in before it was corrupted or lost.
So ask your legaltech if it implements backups and on what cycle. This cycle, or backup frequency, is also known as the “RPO”: Recovery Point Objective. This is the maximum duration of data recording that it is acceptable to lose, for example, in the event of a breakdown. This concept is complemented by the “RTO”: Recovery Time Objective. This is the maximum acceptable time during which an IT resource may not be functional following a service interruption, or in other words, the time it takes to get back into service.
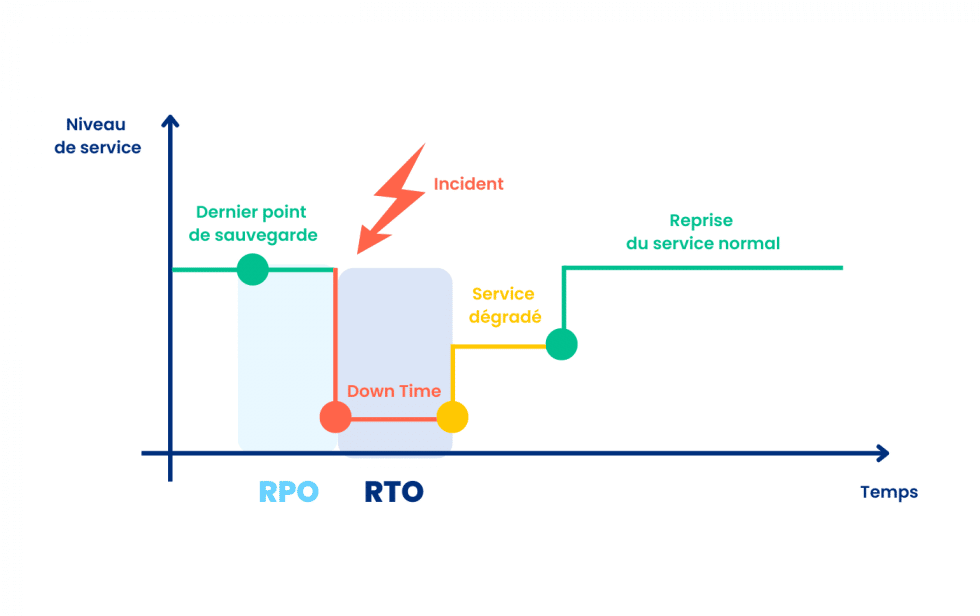
These notions cover a much wider field than the threat of intrusion, theft or hacking, since they will also be useful in the event of a breakdown. The term “resilience” refers to a computer system’s ability to continue operating in the event of any incident.
On the user side: managing access rights
Exchanging ideas with your software partner is good. Implementing your own best practices is even better. To complete this overview of contract data security, here’s a simple tip to apply within your contract management and analysis software.
The principle of segregation, as we saw above with multi-tier infrastructures. Beyond infrastructures, you can also compartmentalize your contractual base within the interface itself, simply by managing the access rights of different users. After all, not everyone needs access to all the company’s contracts.
In DiliTrust, you can grant access rights by team or by user, and levels of access rights (read, modify…), both when generating the contract and when monitoring it in your contract database. Managing user rights in your software is an additional security measure that’s entirely up to you. What’s more, this feature facilitates processes specific to each business line. So why not make the most of it!
Finally, don’t forget about the suspension and/or transferability of rights when a team member leaves the company or moves internally. You have two options: either you need to think about modifying the user’s access, application by application (which can be both restrictive and a source of error), or you can use SSO (Single Sign-On), a method which centralizes user rights and thus makes the modification only once for all the applications to which the user was connected.
Now you know what you need to do to protect your contracts against threats. And if you still have any doubts, do the right thing: simply talk to your IT team and your LegalTech!
Would you like to find out more?
*malware: malicious software designed to damage your computer systems and data.


